
Ransomware is making the news on a regular basis (and gradually turning into an information security meme) due to its increasing popularity among internet criminals. Infections on mission critical machines can bring down important infrastructure, cripple companies, and cause chaos. We’ll take a look at how ransomware works and what it can mean for different users. Finally, we’ll discuss ways to prevent infection.
What Is Ransomware?
At its core, ransomware is a class of malicious software that denies access to information or capabilities until certain conditions are met. Ransomware usually encrypts data that resides on accessible storage locations after getting instructions from a command and control server. Some versions threaten file deletion after a certain period of time. All ransomware demands a fee for reinstatement of user privileges. Bitcoin and other cryptocurrencies are regularly used for billing victims due to their anonymous nature.
Ransomware’s Effects
The impact of ransomware depends on a few different factors. In worst case scenarios, infections can end lives. In best case situations, ransomware will be a mild annoyance. We’ll look at a real world event to kick things off..
Businesses are the primary target of ransomware, as service disruptions incentivize payment. A perfect example came to light this month when 16 U.K. National Health Service hospitals were broadsided by a slew of ransomware infections. The lockout resulted in diverted patients and other significant lapses in service.
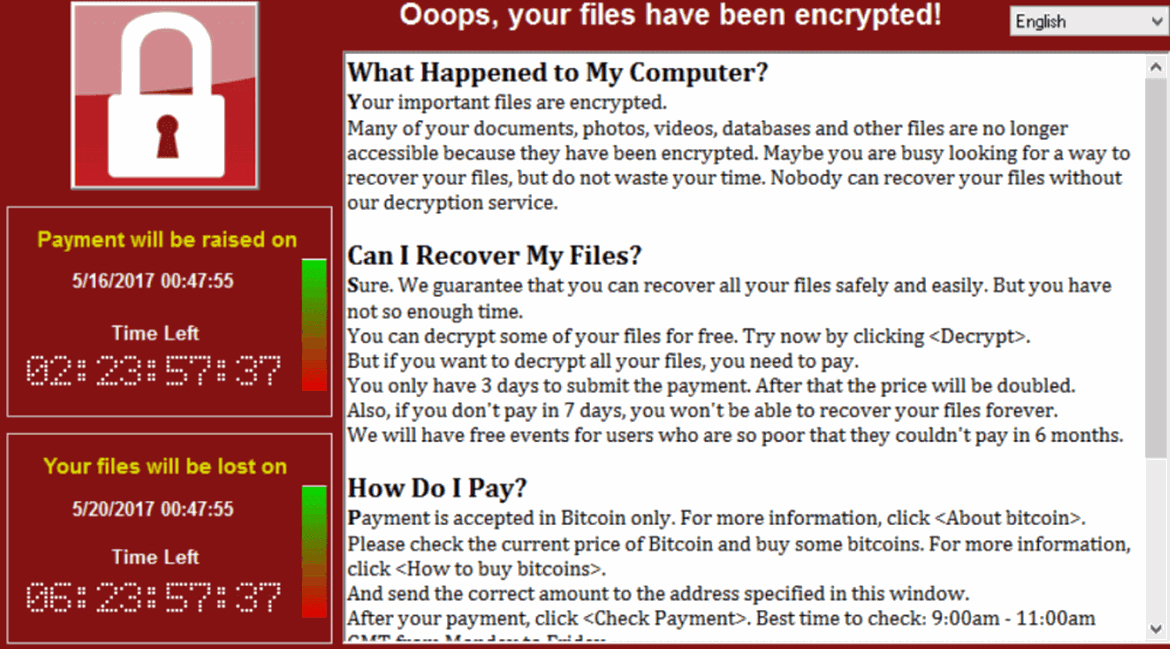
For most health care institutions or businesses, such a disruption would result in lost revenue and a damaged brand. In addition, permanent loss of patient information could occur. Even if the ransom is paid, not all ransomware can properly decrypt networked drives and shares.
Home users are in a slightly different situation. They typically won’t have millions of dollars riding on their data security, but they will suffer from ransomware if no protection is in place. Tax information, music, and photos are encrypted items that most home users would want back. A moderately sized attack could certainly be enough to cripple a small business as well.
Basic Prevention Is Most Effective
The easiest way to prevent malicious software from running on your computer system or network is skepticism. It’s easy to adopt a false sense of security, and that’s the quickest way for criminals to dump programs on your computer. Social engineering, or advanced impersonation and identity theft, is often used to convince users that files are safe. That isn’t its only use, but it’s the one that is relevant to ransomware. Take the following steps, as they will protect you from other forms of attack as well.
• Doubt everything until you confirm its authenticity to a reasonable extent
• When in doubt, do not click on links or open files
• Closely check hyperlinks, email addresses, and downloads to ensure that they are legitimate
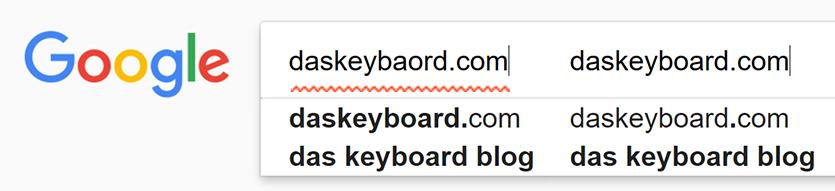
• Simple spelling changes can be used to misdirect users to malicious sites (daskeybaord.com vs. daskeyboard.com)
• Call to confirm before sending sensitive information via email/other online services
Back Up Everything Important
It is vital to back up all of your important files and programs. If an entire system is mission critical, backing up complete hard drive images might be worthwhile. Free utilities (Windows has backup functionality) are available for home use, but enterprise applications are more expensive. They typically involve off-site backups, but on-site backups can also work if they are separated from machines that could be infected.
It’s well worth the hassle, though. Wiping a computer and reinstalling an image takes much less time than attempting to restore partial backups. With platter-based storage becoming cheaper on a regular basis, price per Gigabyte isn’t a significant consideration when compared with the insurance value that backups provide.
Update Your Software and OS Often
Vulnerabilities in software are the entry level target of ransomware and malware. Such programs, once run, must successfully subvert the operating system or associated software using security flaws. There are two different kinds, and each has a different associated risk level.
Zero day exploits are unknown exploits that reside in the wild. The nomenclature is based on the fact that software developers have no time (zero days) to create and implement a fix before a new exploit becomes active. Such attacks are extremely dangerous, as protection options are limited. If a developer has known about a security flaw for a given amount of time, associated exploits are often assigned similar terms. A 20 day exploit, for example, would crop up after a manufacturer had 20 days to patch a flaw.
Once a patch is developed, danger levels drop to nil for updated and uninfected systems. Computers that have already been compromised may not benefit from a patch due to backdoors, or ways for hackers to re-enter systems easily. Those that haven’t been updated will still be vulnerable to infection. One might get lucky with antivirus, but it’s better to rely on a fix from the developer.
The best way to leverage patches is a robust IT infrastructure. At home, it’s easy to set up regular updates (though that doesn’t mean all home users do so). Windows and other programs are quite pushy about the process, so going with the flow is enough in most cases. Other programs and utilities may require manual checks or update utilities.
In businesses, outdated software and operating system components may be unavoidable due to specialized software and sometimes-limited compatibility. Firewalls will solve a few issues in those cases. They can interrupt malicious software when it reaches out to command and control servers, but that only does so much. A well staffed IT department and solid programmers, if you’re writing custom content, should push updates to all company machines on a near-immediate basis. Many operating system management suites exist, and most of them have features that force updates on company computers.
Install Antivirus and Other Preventative Software
Antivirus isn’t perfect. That’s the most important thing to remember. Undiscovered malware, in extreme cases, could run unique code tailored specifically for your company’s hardware or software. If a user prevents malicious files from arriving on a computer in the first place, it mitigates the possibility for an infection with greater finality.
Antivirus suites and programs like Malwarebytes will, however, help supplement security during gaps between patches. It will also pick up known threats and malware that could still have negative affects on your system. Ensure that your choice has process monitoring and file scanning utilities. Finally, find a suite that balances system resource usage and protection. Some are notorious resource hogs. McAfee is no longer the best product on the market, for example. Avast provides decent protection for home users, but businesses will likely want to investigate bulk deals.
Check Your Processes for Viruses in Two Easy Steps
If your computer seems slow, there’s an easy way to check your processes for virus activity. Process Explorer, a Microsoft-designed tool, allows you to view all active processes on your computer and check them against 60+ antivirus programs. In a recent update, it integrated functionality from a Google subsidiary called VirusTotal. VirusTotal essentially pulls together 50 or more antivirus databases from various companies. Users can upload suspicious files to see if they contain malicious code. There is a bulk checking option in Process Explorer, and that’s what we’ll focus on.
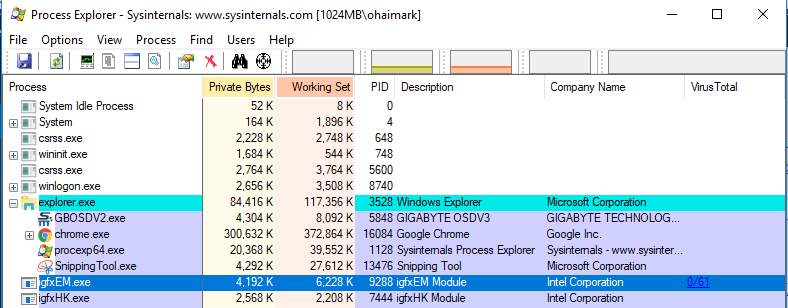
1. Download and run Process Explorer
The executable files will arrive in a zipped folder. Find the saved zip archive — which is probably in your downloads folder — and unpack it. Inside, you’ll see two versions of Process Explorer. If you have a modern computer, you’re probably safe using the 64 bit version, or procexp64.exe.
2. Check processes against VirusTotal
You can check all of your processes at once by clicking the Options drop down menu, hovering over the VirusTotal.com option, and selecting Check VirusTotal.com.
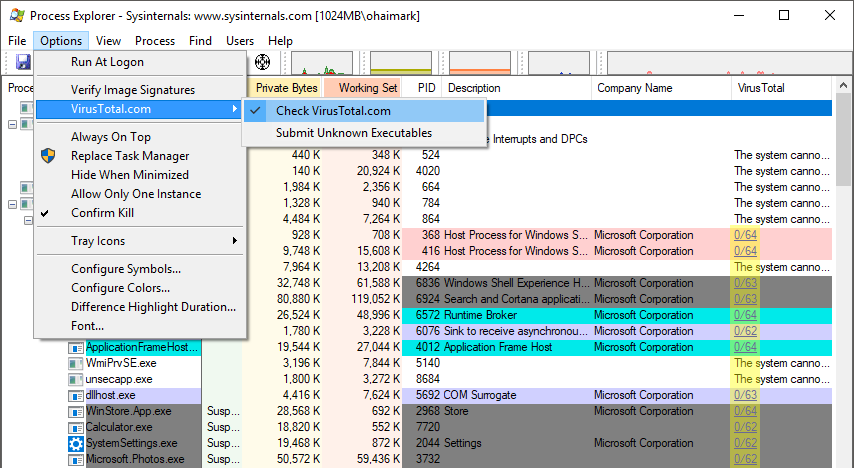
You’ll need to read a user agreement, which may appear in your web browser, before proceeding. Process Explorer will submit each process’ file hash (number used to compare files) to VirusTotal. When the comparison is complete, a pair of numbers (#/##) will appear in the far right column of Process Explorer. If a submitted process is malware, the first number should register a value greater than 1. 1/64, for example, would indicate that the file is considered malicious by one antivirus contributor. If the value of the first number is zero (0/##), it should be safe.
If you would like to submit individual processes that seem suspicious, as opposed to a shotgun approach, it’s pretty easy. Right click on a process and left click “Check VirusTotal” in the resulting drop down menu.
Wrapping Up
We’ve taken a quick look at ransomware, its effects, and ways to prevent infection. Das Keyboard utilizes the tactics mentioned above. We hope that home users and businesses will follow suit. Data security is critical to our business and our customers, so special attention is paid to the software and firmware in our products.
Feel free to leave thoughts, questions, and additional tips in the comments. We’d also like to hear from you on Twitter.
